Cyber Security And Risk Management Articles

Wikipedia articles will not be accepted.
Cyber security and risk management articles. Cybersecurity reports by cisco show that thirty one percent of organizations have at some point have encountered cyber attacks on their operations technology. 21 sep 2020 24 sep 2020 online virtual. Please use your own words. Dashboards are used in thousands of businesses every day.
Based on your article review and the assigned reading discuss the relationship between cybersecurity and risk management. Sessions will include interactive incident management session best practices to integrate risk and it and understanding cyber risk and human behaviour. When it comes to cybersecurity organizations face a future in which it s best to prepare for worst case scenarios. Dashboards are used in thousands of businesses every day.
Improve your ability to manage cyber risk. As an it manager discuss how you will use the concepts discussed in the four articles in the management of it risks within your company. Summarize the two 2 articles in 300 words or more. Security risk management security risk management provides a means of better understanding the nature of security threats and their interaction at an individual organizational or community level standards australia 2006 p.
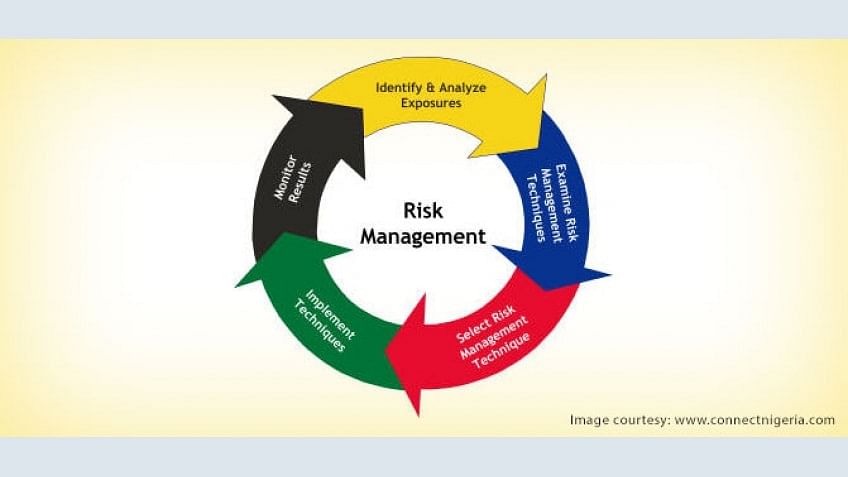
Generically the risk management process can be applied in the security risk management context. As an it manager discuss how you will use the concepts discussed in the four articles in the management of it risks within your company. Summarize the two 2 articles in 300 words or more. Because the purpose of cybersecurity is to support and protect business functions it must be aligned with business objectives and appropriately funded to match risks.
Cybersecurity should be integrated into the overall risk management process of every government organization e g jurisdiction department or agency. As an it manager discuss how you will use the concepts discussed. Read at least two 2 academically reviewed articles on cyber security and risk management and complete the following activities. Please use your own words.
Read at least two 2 academically reviewed articles on cyber security and risk management and complete the following activities. Base on your article review and the assigned reading discuss the relationship between cyber security and risk management. Professor may check originality of all posts. Furthermore cyber attacks were the number one concern of executives in european and other developed countries according to a recent.
Top 10 cybersecurity risk for 2019 the cyber threat environment is becoming more dangerous every day. Wikipedia articles will not be accepted. Base on your article review and the assigned reading discuss the relationship between cyber security and risk management. 5 fundamentals in cyber risk management.